DNS over HTTPS (DoH): Definition, Implementation, Benefits, and More
DNS Security - Endpoint
With a powerful blend of cybercrime intelligence, advanced machine learning, and AI-based prevention, Heimdal DNS Security Endpoint ensures unparalleled accuracy in proactively protecting your organization from future threats. Keep your business secure and stay one step ahead with our trailblazing DNS security solution.
Prevent Tomorrow’s Threats Today with Heimdal’s Endpoint DNS Security Solution
Experience absolute peace of mind for administrators and unleash limitless creativity for all users, whether they’re working on-site or remotely, with Heimdal DNS Security Endpoint.
Our powerful DNS security tool scans your users’ online traffic in real time, effectively blocking infected domains and thwarting communication with cybercriminal infrastructures. Enjoy secure and seamless Internet browsing without compromising system performance, thanks to our solution’s minimal system footprint.
Elevate your protection to the next level today.
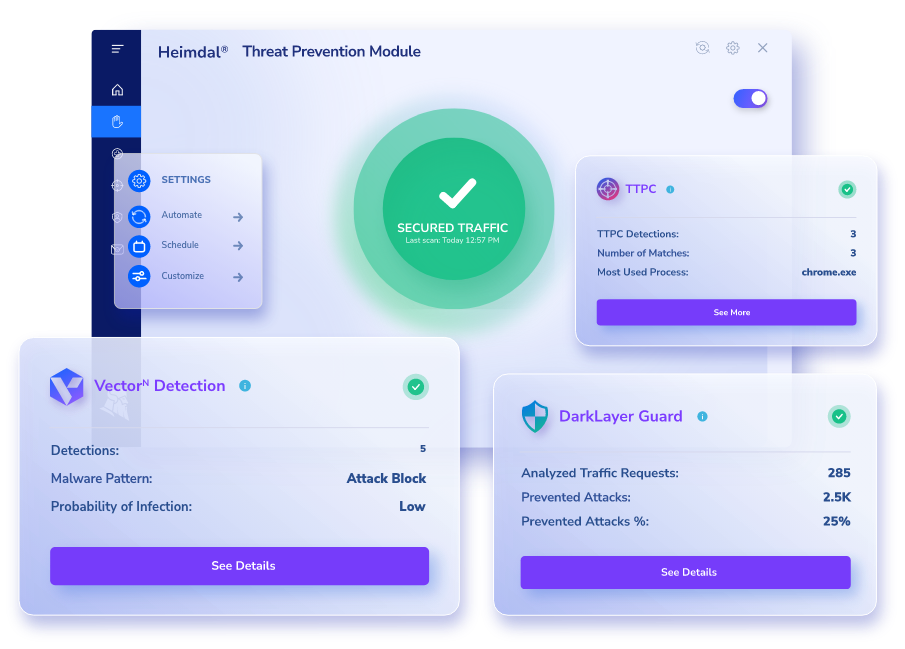
DNS, HTTP and HTTPs Traffic
Filtering
91% of online threats leverage the DNS to exploit vulnerabilities. Heimdal’s DNS Security Endpoint effectively identifies emerging and concealed cyber-threats at all connection levels, putting an end to cyberattacks that often bypass traditional antivirus measures.
Machine
Learning-Powered Prediction
DNS Security Endpoint has 96% accuracy in predicting future threats with our state-of-the-art *Predictive DNSPat.Pend. technology, using applied neural networks modelling that allows you to confidently own your company’s DNS governance setup and hinder all immediate and future cyber-threat scenarios.
Unparalleled
Threat Hunting
Capabilities
Spot malicious URLs and processes, then immediately backtrack the attacker’s origins with a code-autonomous endpoint DNS threat hunting solution. Empower your team with the perfect tools and gain complete visibility and control over your endpoints, all with a minimal system footprint.
*PAT. PEND. - Heimdal's Apparatus and Method for Predicting Malicious Domains EU Patent Application: P025966EP1 US Patent Application: 18333620
Gain Complete Control over Your DNS Environment at Endpoint Level
True DNS over HTTPS Filtering
Threat hunt beyond the limited boundaries of DNS by leveraging the true powers of DNS over HTTPS traffic filtering to stop cyberattacks, hidden malware, and threats abusing legitimate tools, applications, or cloud services.
Heimdal is the world’s first vendor on the market to integrate true DNS over HTTPS in a product, evolving past the standard rerouting of DNS packages. Threat Prevention gives no quarters to hackers, regardless of the connection protocol, company cyber-awareness status, profile, or industry.
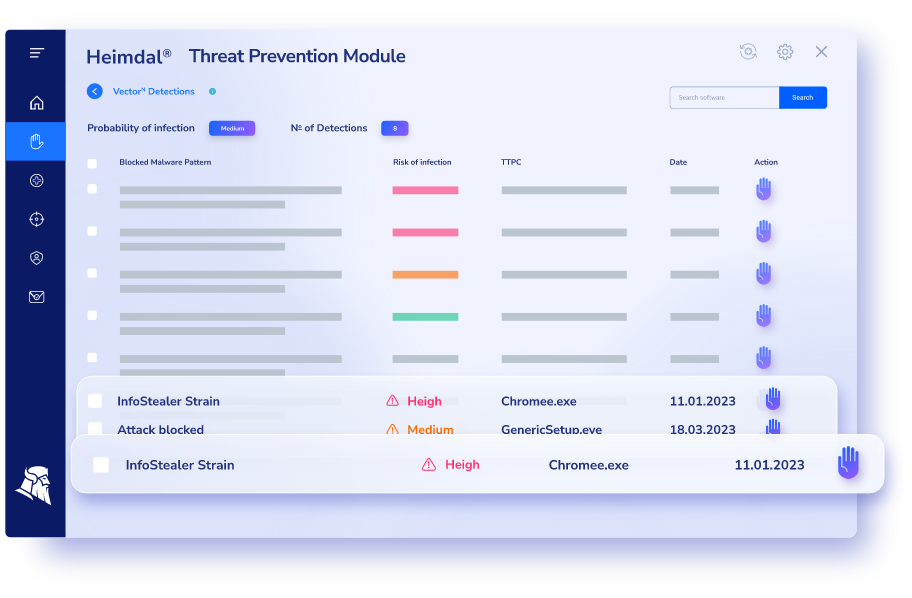
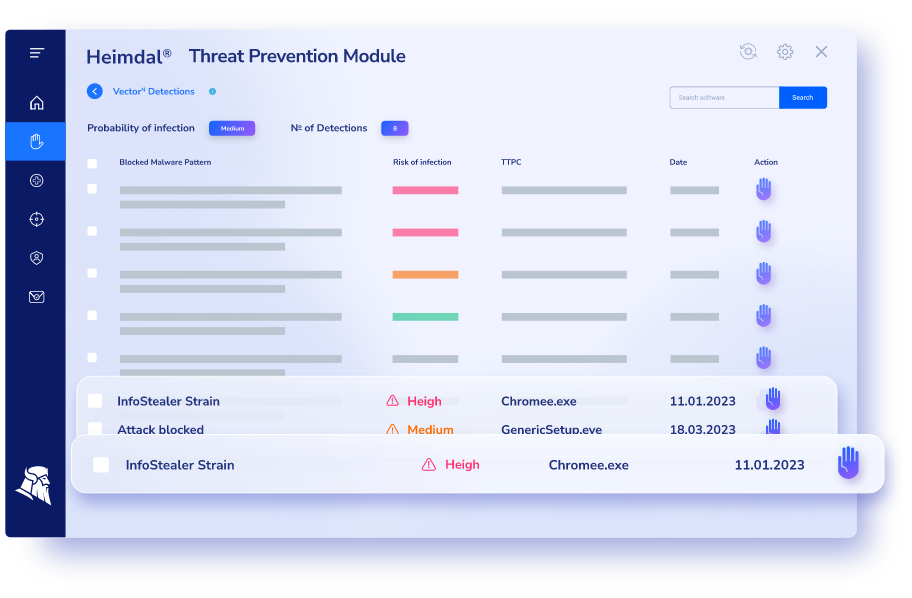
Advanced Malware Detection
Take full control of your DNS, HTTP, and HTTPS communications through unique machine learning-computed threat intel that empowers you to move the needle from traditional antivirus threat detection to a prevent & hunt posture.
Gain unprecedented control over what happens inside and outside your corporate network, eliminating the need to rely on lackluster threat analysis software or hire additional security analysts.

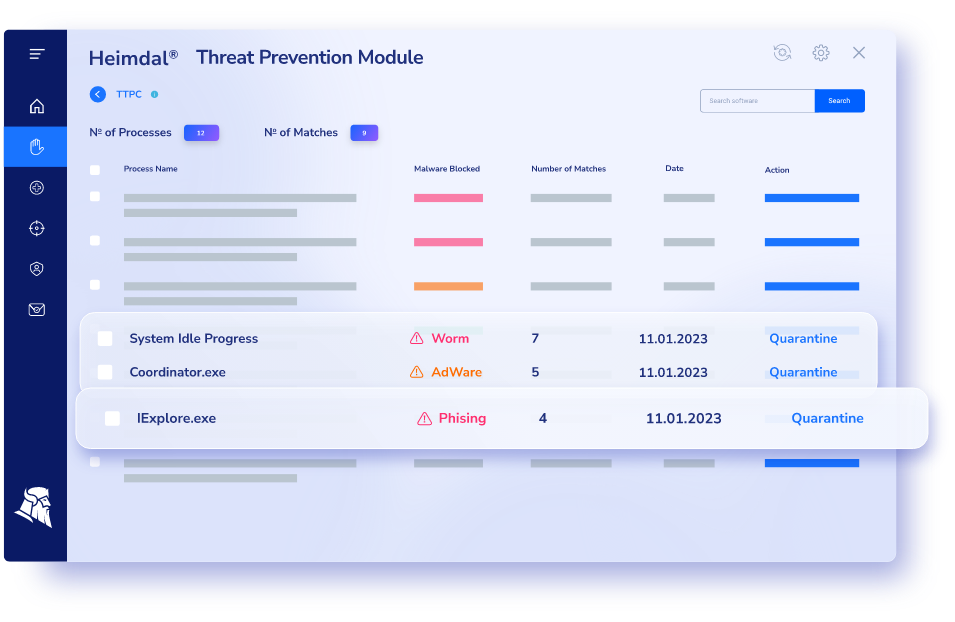
Unparalleled Proactive Protection
Discover the power of best-in-class threat hunting and prevention right at your fingertips, without the burden of managing multiple platforms and outdated pen-testing tools. Our comprehensive DNS Security Endpoint solution is enriched with Cloud Access Security Brokerage (CASB) capabilities.
Unleash the ability to combat insider threats, detect and eradicate shadow IT instances, and neutralize any form of malicious activity linked to compromised accounts. Upgrade your security defenses effortlessly and stay one step ahead of evolving threats.
Cross-Compatibility with Any Security Solutions
Enhance your existing security ecosystem effortlessly with DNS Security Endpoint. Our solution is designed to seamlessly integrate with any other security solutions you may have in place, ensuring a cohesive defense strategy. Deploying Threat Prevention in your environment is a breeze, taking less than an hour to set up.
Leveraging the power of cloud-native threat intelligence, our solution provides robust protection for your critical assets. Safeguard against a wide range of threats, from simple human errors to sophisticated malware campaigns and everything in between.

Take control of your enterprise endpoints and system with Heimdal.
Our DNS Security Endpoint module adds to any Antivirus or Firewall and can be combined with more Heimdal® products to deliver an authentic Endpoint Detection and Response (EDR) stance.
All working together seamlessly from one agent and one unified platform.

Network
Security

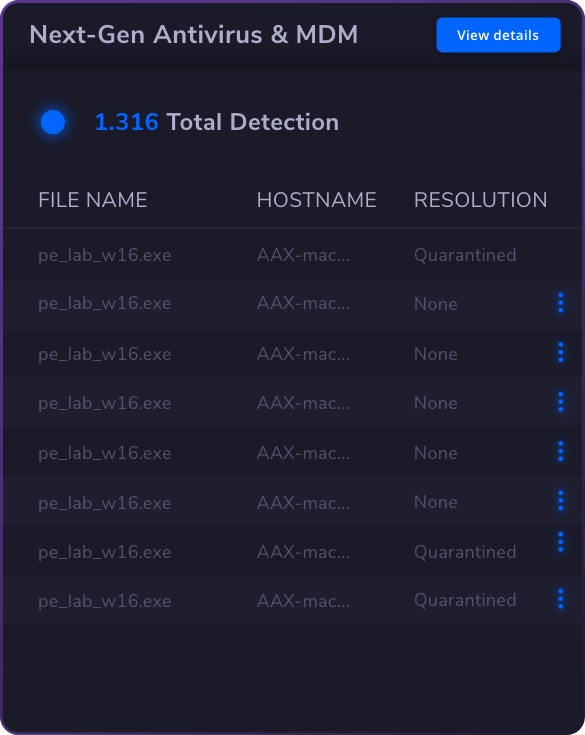
Endpoint
Security

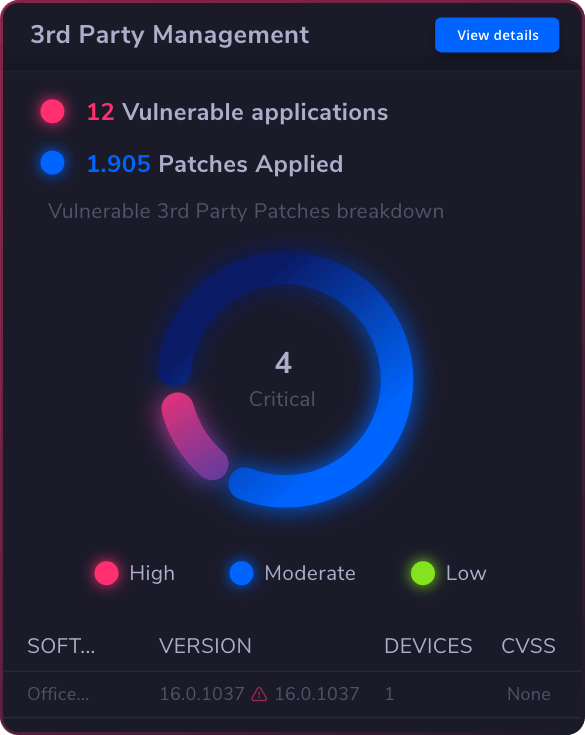
Vulnerability
Management

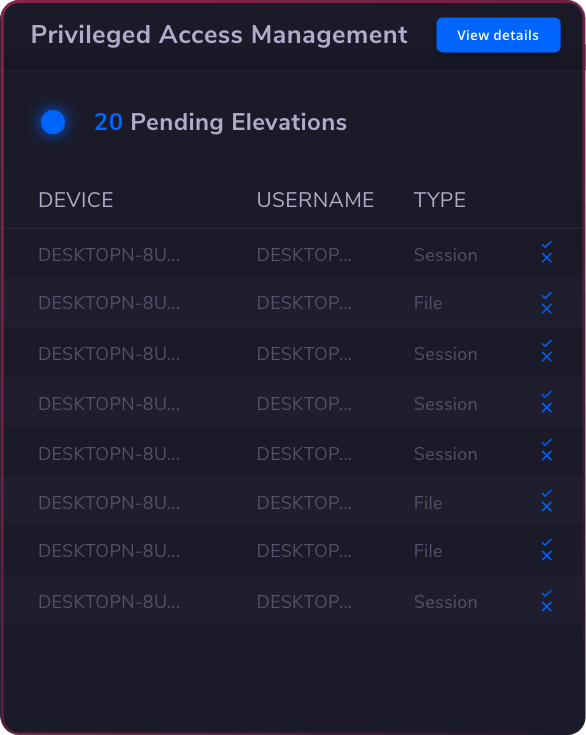
Privileged
Access
Management
Privileged Access Management
Privilege Elevation & Delegation Management Privileged Account & Session Management Application Control
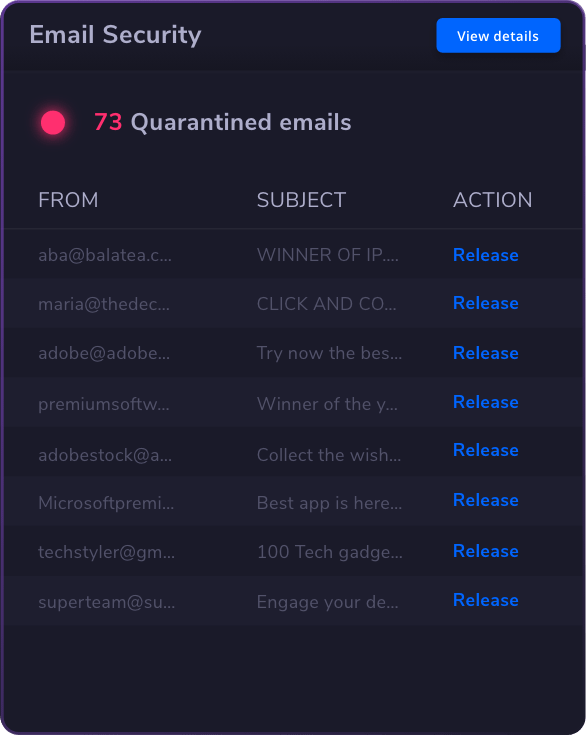
Email &
Collaboration
Security

Threat
Hunting
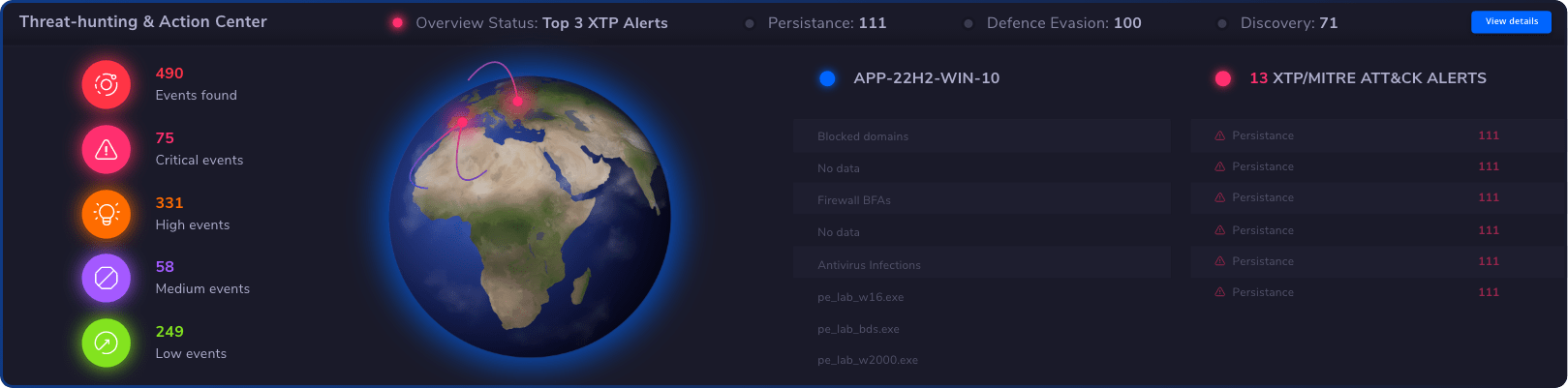
Threat Hunting
Threat-hunting & Action Center
Unified
Endpoint
Management
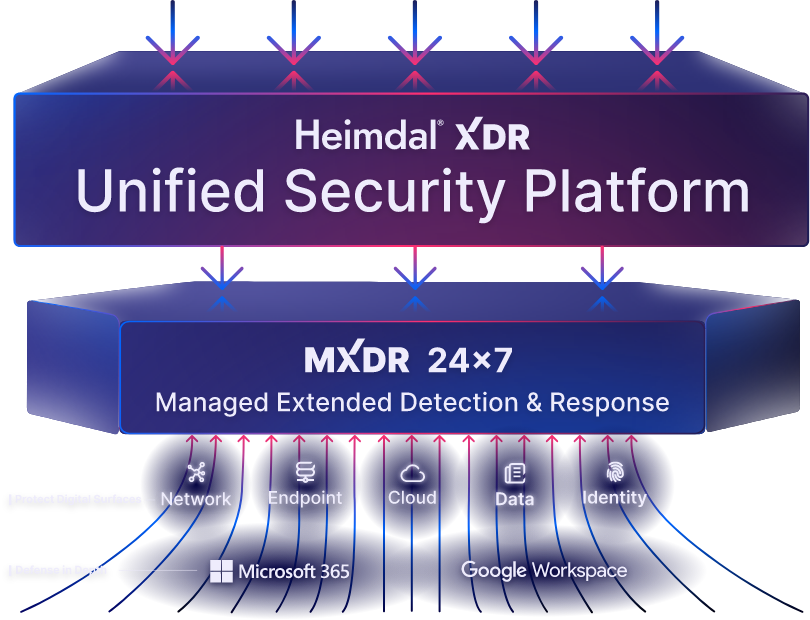
Heimdal XDR
One Platform. Total Security.
One Platform,
Total Security.
Experience the Power of Heimdal XDR the Unified Security Platform that Delivers Comprehensive Protection against Next-gen Threats
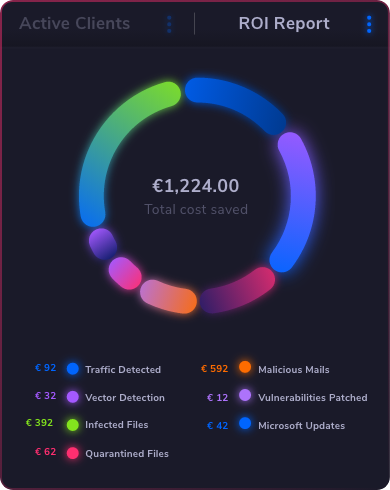
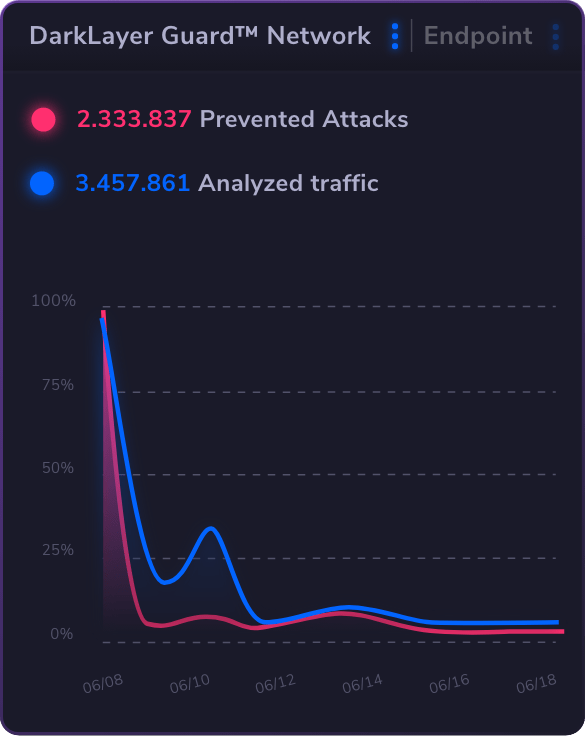
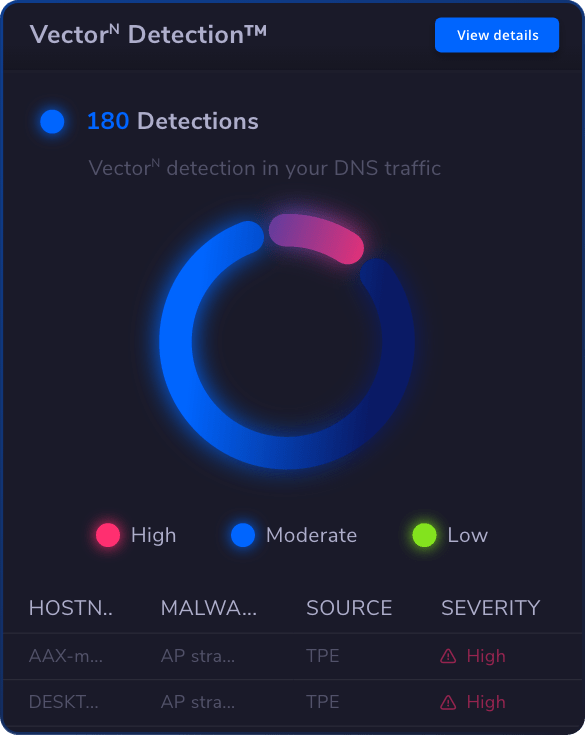

See Heimdal XDR in Action:
Schedule a Live Demo Now!



 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security












 4.8/5
4.8/5

